When was the last time you installed the latest TP-Link firmware update? If you don’t remember, it can be a cause of concern. Numerous security websites have reported that residential TP-Link routers are increasingly being infected by the “Horse Shell” malware developed by the “Camaro Dragon” hacking gang. This group is allegedly backed by the Chinese government and is used to target European foreign policy institutions.
In order for hackers to launch assaults that seem to come from home networks, a backdoor virus is used in a malicious firmware that is specifically created for TP-Link routers.
“It is important to note that this kind of attack is not specifically targeted at sensitive networks, but rather at regular residential and home networks,” mentioned a report from the Check-Point. “Therefore, infecting a home router does not necessarily imply that the homeowner was a specific target; rather, it may simply suggest that their equipment served as a tool for the attackers to use in order to accomplish their goals,” it added.
Threat actors can use the device as a SOCKS(Socket Secure) proxy to relay communications between devices, conduct shell commands, upload and download files, and more thanks to the malware that has been installed.
Check Point Research found the Horse Shell TP-Link firmware insertion in January 2023 and claims that the hackers’ activities coincide with those of the Chinese “Mustang Panda” hacking gang recently mentioned in Avast and ESET publications.
Despite the similarities and substantial overlap with Mustang Panda, Check Point counts this activity independently under the name “Camaro Dragon” for the sake of the activity cluster.
The attackers’ server IP addresses, requests with hard-coded HTTP headers discovered on various Chinese websites, multiple errors in the binary code indicating a non-English author, and similarities in the trojan’s functionality to the APT31 “Pakdoor” router implant were used to attribute the attack.
TP-Link firmware Update Implant
Although Check Point has not figured out how the attackers get the malicious firmware image onto TP-Link routers, they speculated that it might be via exploiting a flaw or by brute-forcing the administrator’s credentials.
A threat actor can remotely install a TP-Link firmware update with a custom firmware image once they have administrative access to the management interface.
Through examination, Check Point discovered two examples of modified TP-Link router firmware images, each of which contained several changes and file additions.
The Kernel and uBoot parts of the malicious and valid TP-Link firmware were identical, according to Check Point’s analysis. But, a unique SquashFS filesystem was used by the malicious firmware that contained extra malicious file components as a part of the Horse Shell backdoor malware implant.
“We use the internal name Horse Shell for some of it, so we use it for the implant as a whole,” explained CheckPoint. “The implant gives the attacker three key functionalities: a remote shell, file transfer, and tunnelling,” they added.
The software also alters the administration web interface, making it impossible for the owner of the device to flash a fresh image of the router’s firmware and assuring the infection’s persistence.
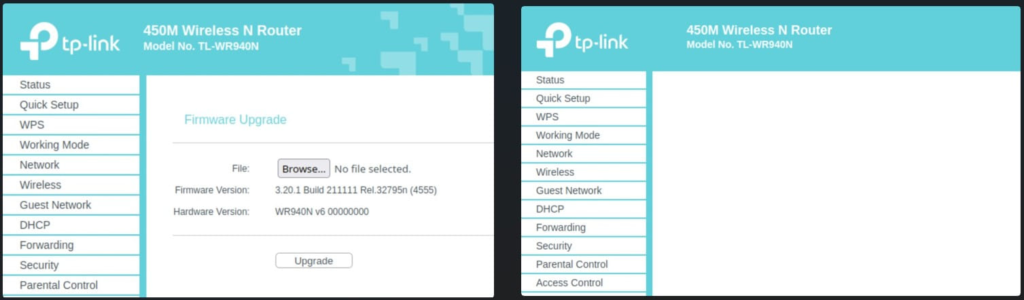
Standard Firmware (left), and Trojanized (right) preventing firmware updates
Horse Shell Backdoor Implant- How it works?
When the Horse Shell backdoor implant is first activated, it will instruct the OS to turn the application into a daemon that runs in the background and not terminate it when SIGPIPE, SIGINT, or SIGABRT commands are issued.
The victim’s machine profile, comprising the user name, OS version, time, device information, IP address, MAC address, and supported implant capabilities, will then be sent by the backdoor over a connection to the command and control (C2) server.
Now, while waiting for one of the following three orders, Horse Shell will quietly run in the background:
- Start a remote shell that gives the affected device’s compromised threat actors complete access.
- Complete file transfer tasks, such as downloading and uploading files, basic file modification, and directory enumeration.
- Start tunnelling to conceal the C2 server address and obscure the network traffic’s origin and destination.
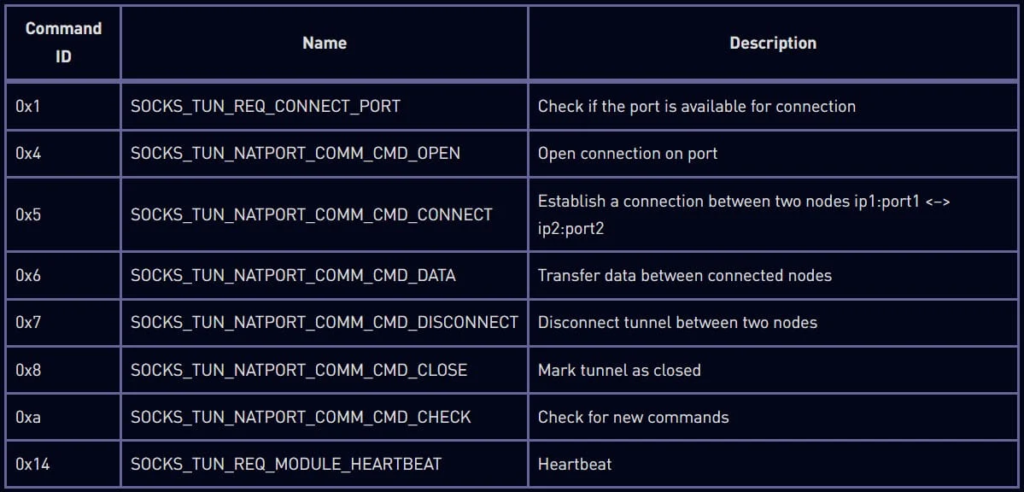
Tunneling Sub-Commands; Source- CheckPoint
The Horse Shell firmware implant, according to the researchers, is firmware-agnostic, meaning it might theoretically function in firmware images for other routers made by various vendors.
It is not uncommon to see state-sponsored hackers target unsecured routers, which are frequently the target of botnets used in DDoS assaults or cryptocurrency mining. This is due to the fact that routers are frequently disregarded while putting security measures in place and can serve as a covert launcher for attacks, masking the attacker’s origin.
Users are encouraged to make the latest TP-Link firmware update and keep their devices at the most recent version in order to avoid any security gaps and secure the default admin password. But even more crucially, limit access to the device’s admin panel to the local network alone by disabling remote access.
A Recurring Theme of Events
State-sponsored threat actors are increasingly attacking edge network devices; Chinese hackers have previously used custom firmware implants to target Fortinet VPN and SonicWall SMA routers as well.
More recently, Russian state-sponsored threat actors were also breaking into Cisco routers to install specialised malware, according to recent warnings from the UK NCSC and US CISA cybersecurity organisations.
Threat actors can utilise these devices to steal data, spread laterally, and carry out additional attacks with less chance of being discovered because they frequently do not support EDR (Endpoint Detection and Response) security solutions.
According to Mandiant CTO Charles Carmakal, “there is a recurring theme of continued China-nexus cyber espionage focus on network appliances, IOT devices, etc. that don’t support EDR solutions.”
Network administrators must therefore immediately apply all security updates to edge devices and avoid making management panels accessible to the public.
Stick to routerloginsupport.com for more such informational updates. If you like it, share the news with your friends, connections and family. If you’ve been a victim of router hacking, reach out to our team to discuss the possibilities of retrieving access to it, now!
Image Source : https://www.bleepingcomputer.com/news/security/hackers-infect-tp-link-router-firmware-to-attack-eu-entities/